How To Wireshark Encrypted Traffic

Data packets can be viewed in real time or analyzed offline.
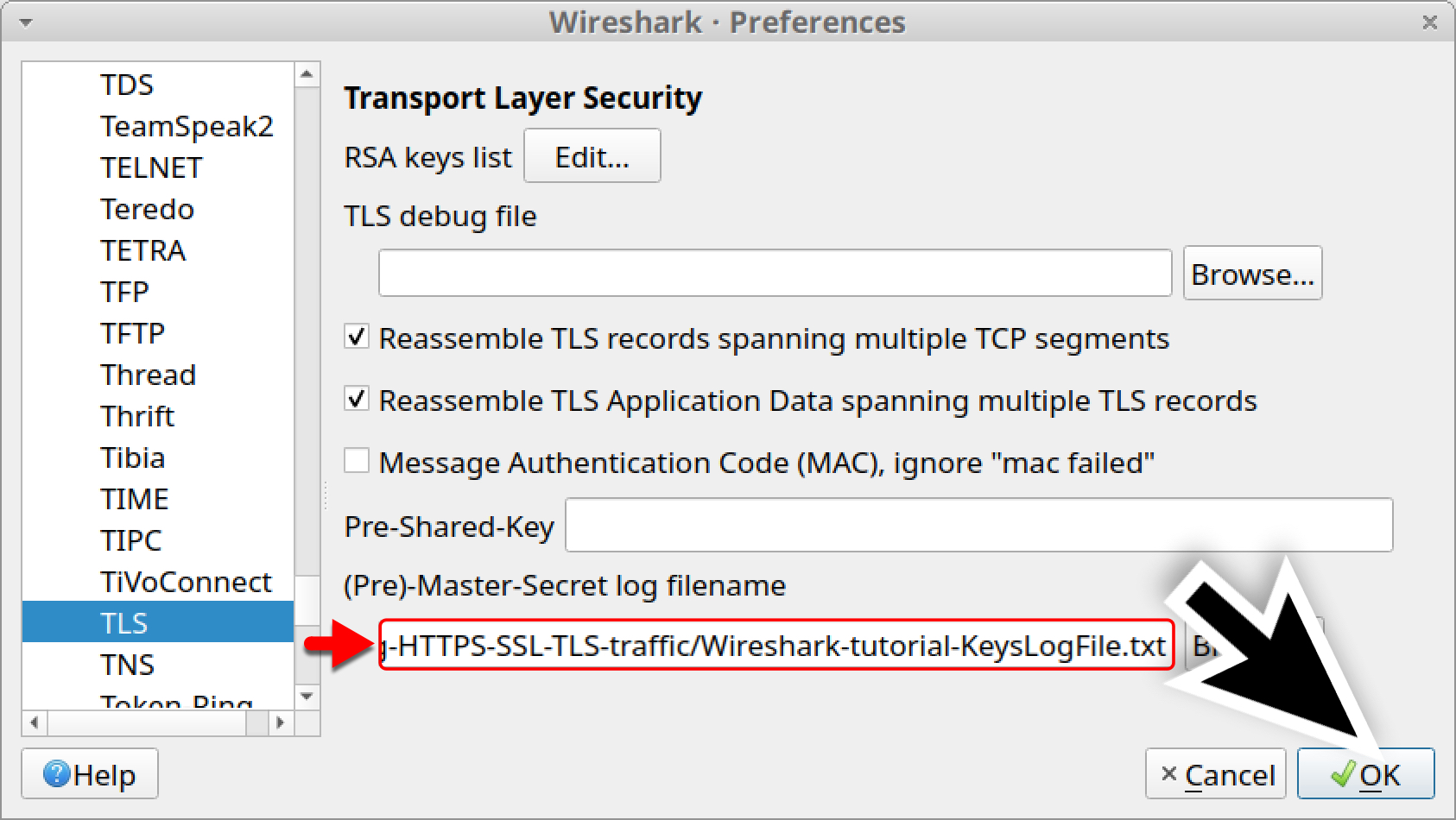
How to wireshark encrypted traffic. Encryption key log file. Actually wireshark does provide some settings to decrypt ssl tls traffic. Wireshark is a commonly known and freely available tool for network analysis. Press to add an entry of the ssl tls traffic that needs to be decrypted. The first step in using it for tls ssl encryption is downloading it from here and installing it.
Some tls versions will allow you to decrypt the session using the server private key. There are two methods to so this. Select edit preferences. Wireshark supports dozens of capture trace file formats including cap and erf. In some cases umbrella support may request that you disable dns encryption to see the dns traffic between the roaming client and umbrella cloud.
Load the private key into wireshark in pem pkcs format. Go to edit preferences. Following the transmission control protocol tcp stream from a pcap will not reveal the content of this traffic because it is encrypted. Open the protocols tree and select ssl. Prior to reproducing the issue ensure that wireshark is properly configured to decrypt ssl tls traffic.
Integrated decryption tools display the encrypted packets for several common protocols including wep and wpa wpa2. Wireshark has an awesome inbuilt feature which can decrypt any traffic over a selected network card. However i can only see encrypted network packets in wireshark because all browsers only support http 2 that run over tls. The other thing that you ll need to do before decrypting tls encrypted traffic is to configure your web browser to export client side tls keys. Using the private key of a server certificate for decryption.
An encryption key log is a text file.